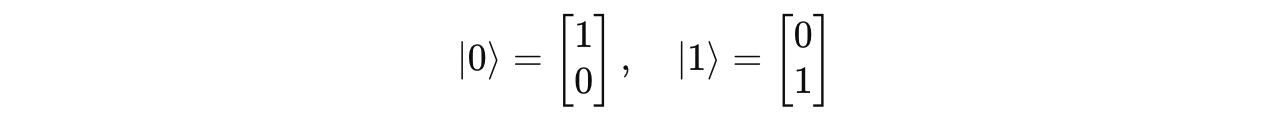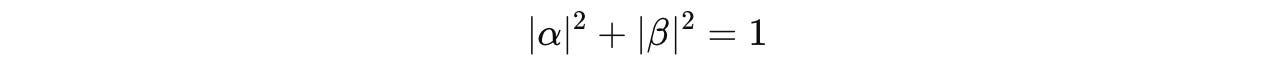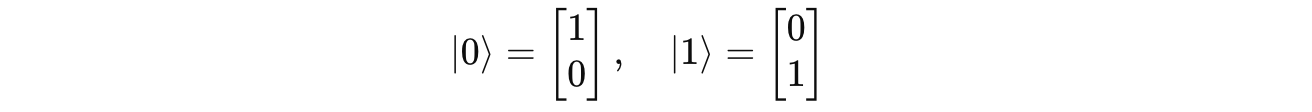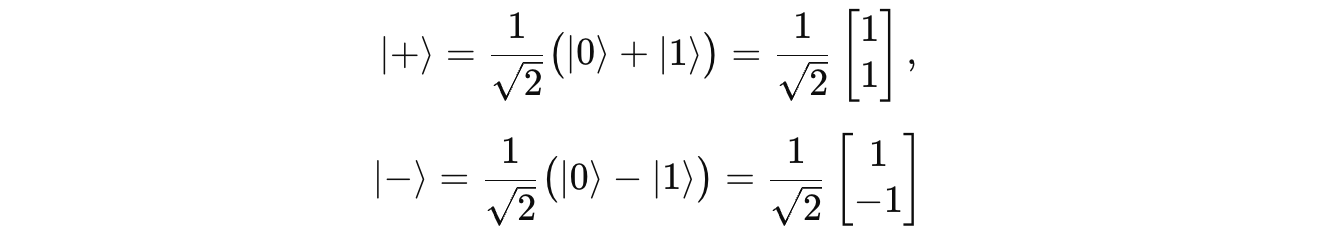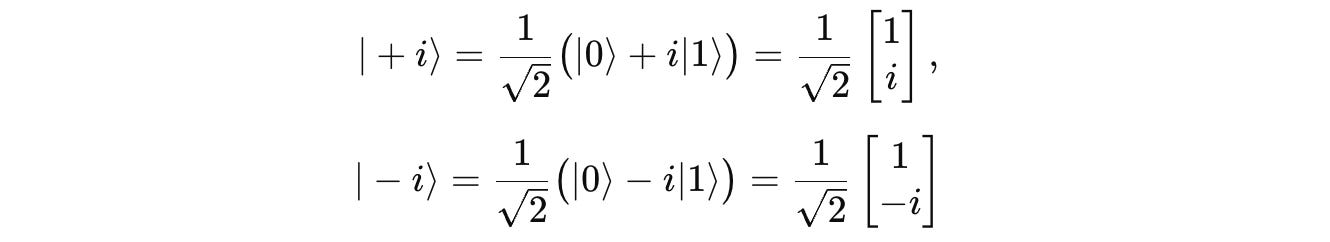The BB84 Protocol Explained From Scratch
A deep dive into the BB84 protocol, a quantum key distribution protocol that lets two parties share a secret key for secure communication.
The BB84 algorithm is named after Charles Bennett and Gilles Brassard, and is the first quantum cryptographic protocol, developed in 1984.
This algorithm is intended to be used to share a secret key between two parties securely. This secret key can then be used to encrypt and decrypt messages between these parties (in a method called Symmetric encryption) for secure communication.
Here’s a lesson where we understand how this protocol works in depth, learning everything from the ground up.
Let’s begin!
A Refresher On Quantum Mechanics
In quantum mechanics, the state of a quantum system is described using a Ket vector.
A qubit’s state is a superposition of two basis ket vectors.
For example:
where the basis ket vectors are:
and α and β are complex numbers called Probability amplitudes, whose squared magnitudes (α², β²) give the probabilities of measuring the qubit in basis states |0> and |1>, respectively.
These magnitudes satisfy the normalization condition:
A qubit lives in a 2-D complex Hilbert space.
To visualise this 2-D complex Hilbert space on a 3-D real (not complex) space and make it more intuitive, we use something called the Bloch Sphere.
The Bloch sphere is a geometric representation of a single qubit’s state.
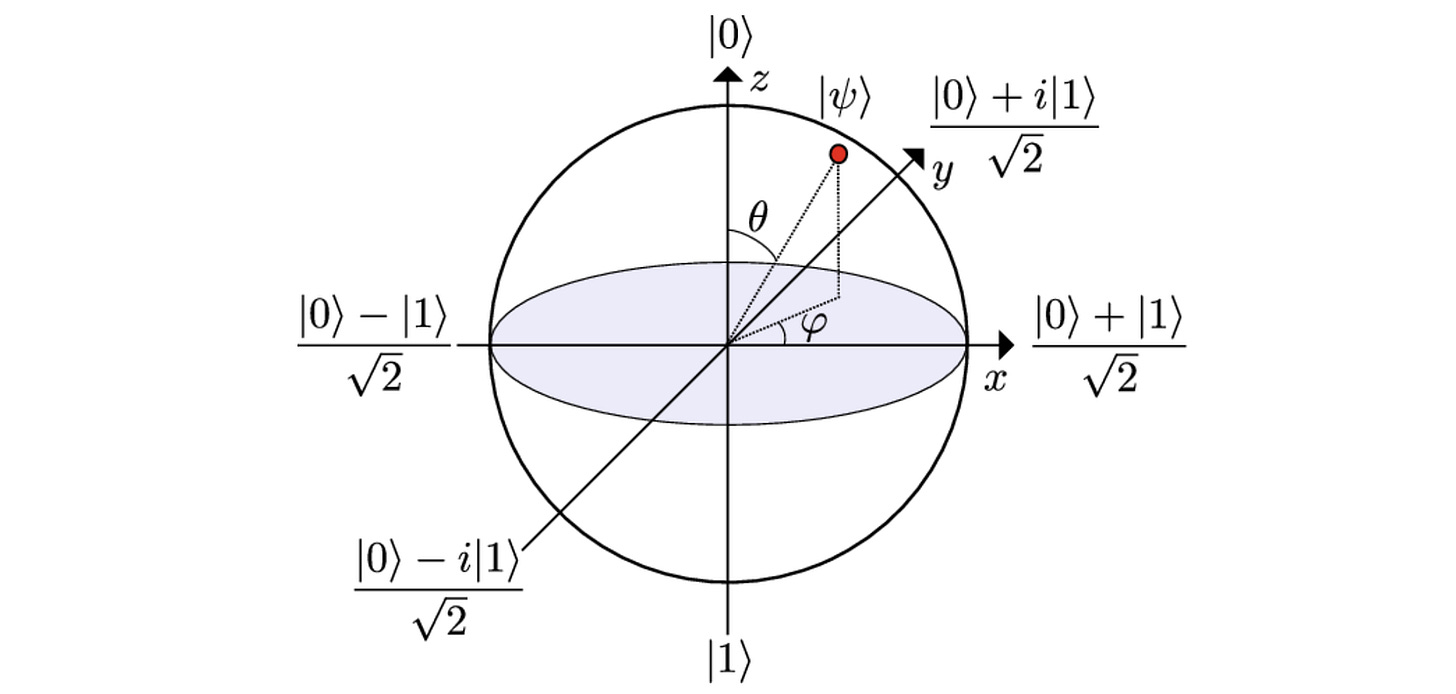
On a Bloch sphere:
The north (positive Z-axis) and south (negative Z-axis) poles represent the basis states
|0>and|1>, respectively.
The positive and negative X-axis represent the Hadamard basis states
|+>and|->, respectively.
The positive and negative Y-axis represent the basis states
|+i>and|-i>, respectively.
(If you’re new to these terms and want to understand them thoroughly, it is recommended that you check out the previous lessons on “Into Quantum”.)
A Refresher On Encryption Methods
Consider two parties, Alice and Bob, who want to communicate with each other securely.
They will use Encryption, which is the process of using mathematical techniques to scramble information in such a way that only the parties who have the key to unscramble it can access it.
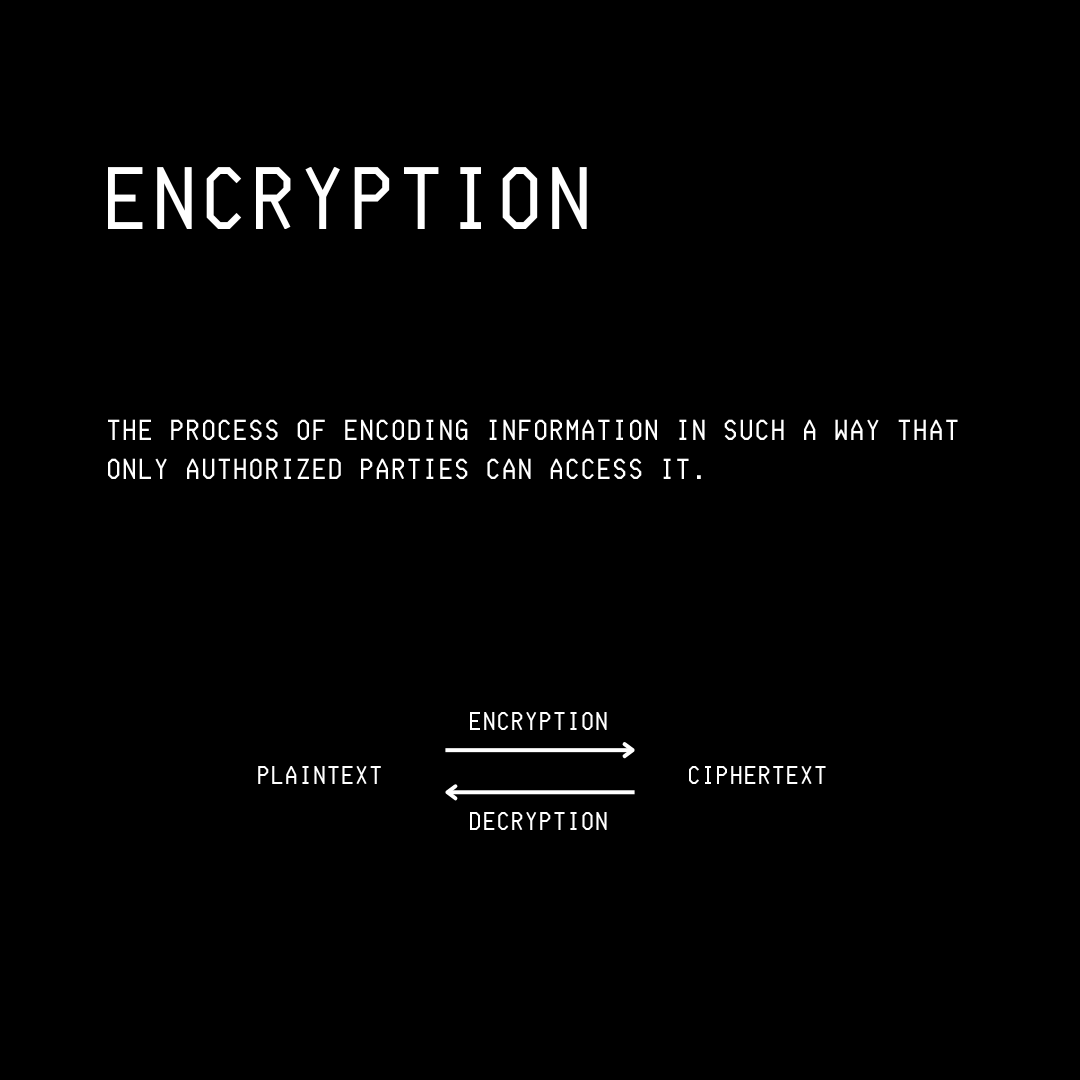
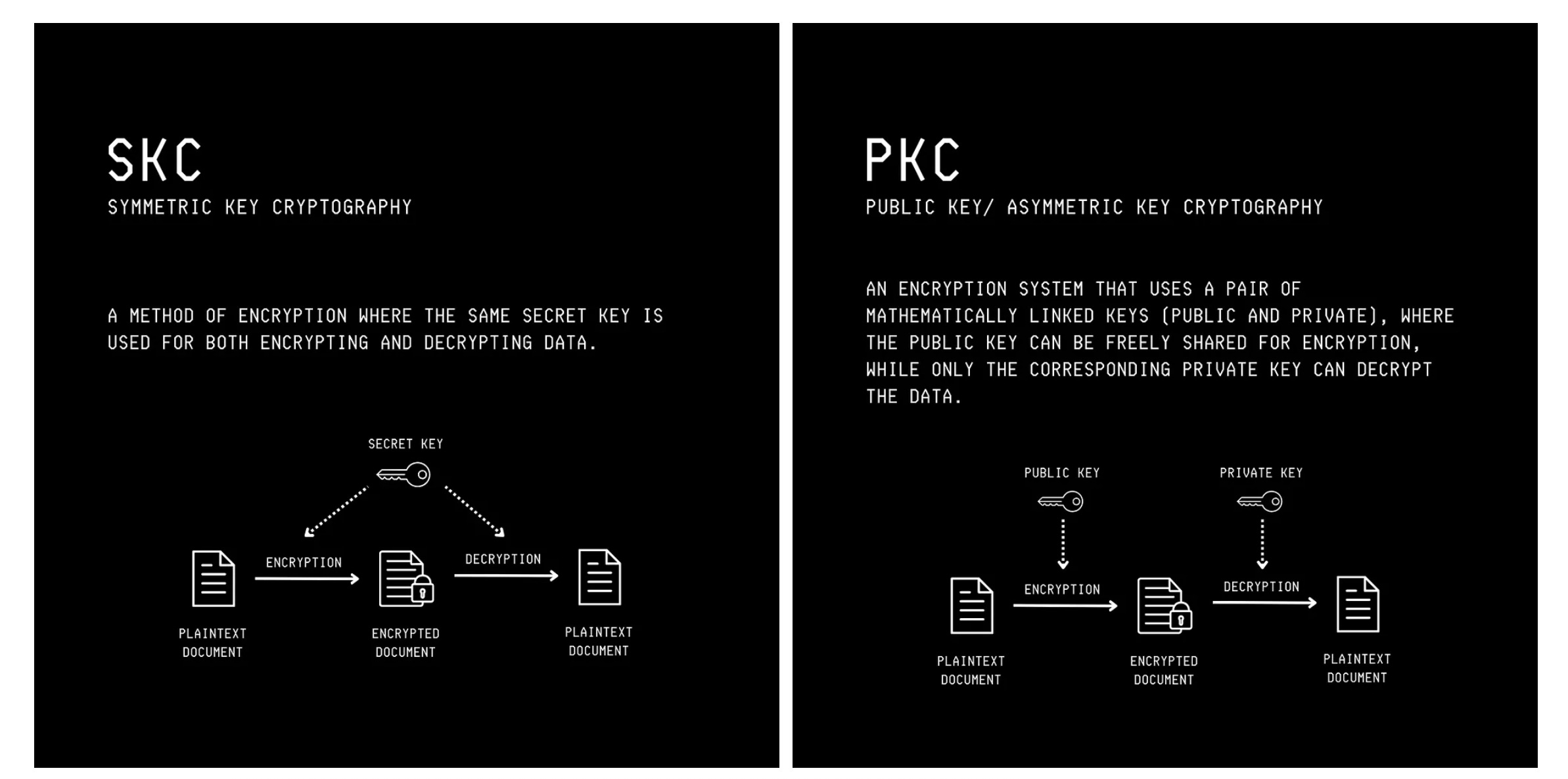
These are two ways of performing Encryption:
1. Symmetric key cryptography: where the same secret key is used for both encryption and decryption of messages.
2. Public/ Asymmetric key cryptography: where two different keys are used. A public key is available to everyone for encryption, and a private key is kept secret for decryption of messages.
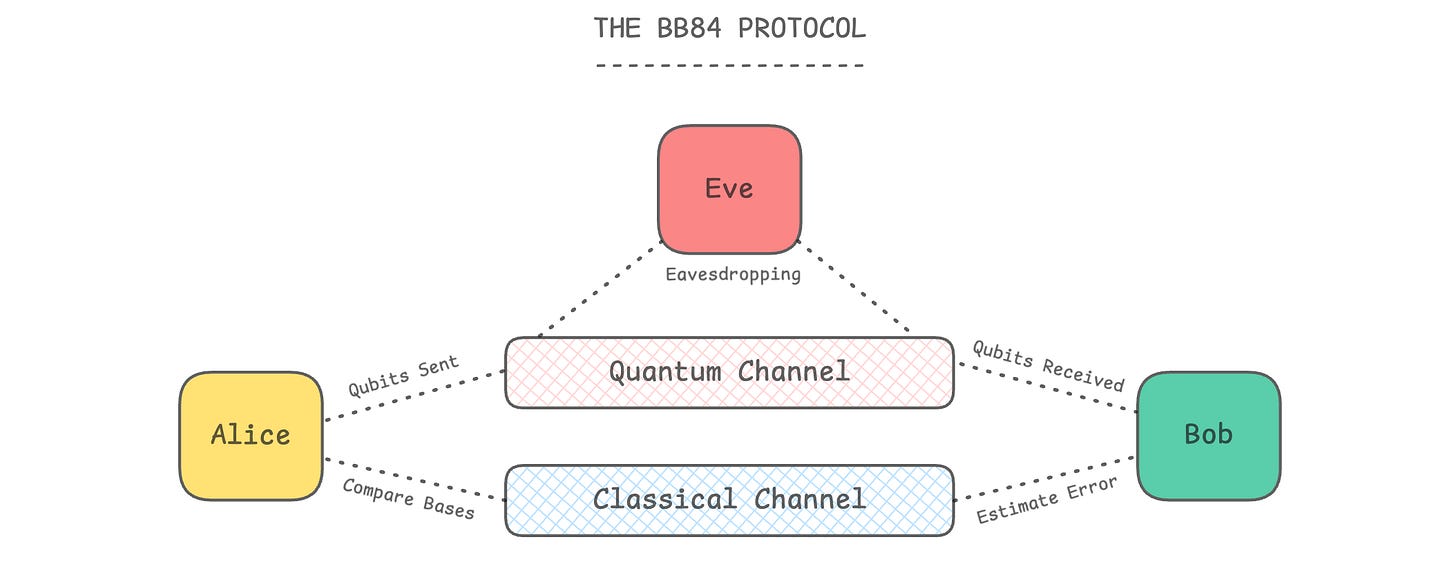
Next, To The BB84 Protocol
The BB84 Protocol is a method by which Alice and Bob can share a secret key over a quantum channel to perform encryption later on using Symmetric key cryptography.
But why a Quantum channel?
This is due to its unique properties (thanks to quantum mechanics), which we will soon learn about, that ensure that the key distribution remains secure.
Let’s start learning about the details of this protocol.
When using the BB84 Protocol, both Alice and Bob use two sets of bases (singular ‘basis’) as follows:
|0>and|1>(Z-axis basis)|+>and|->(X-axis basis)
The steps taken are as follows.
Step 1: Alice Creates A String Of Bits
Alice starts by randomly creating a string of classical bits (0 or 1).
Let’s say, this is a bit string 0 1 1 0.